|
Getting your Trinity Audio player ready...
|
Crypto Hacks and Scams in Q3 2023: A Comprehensive Overview
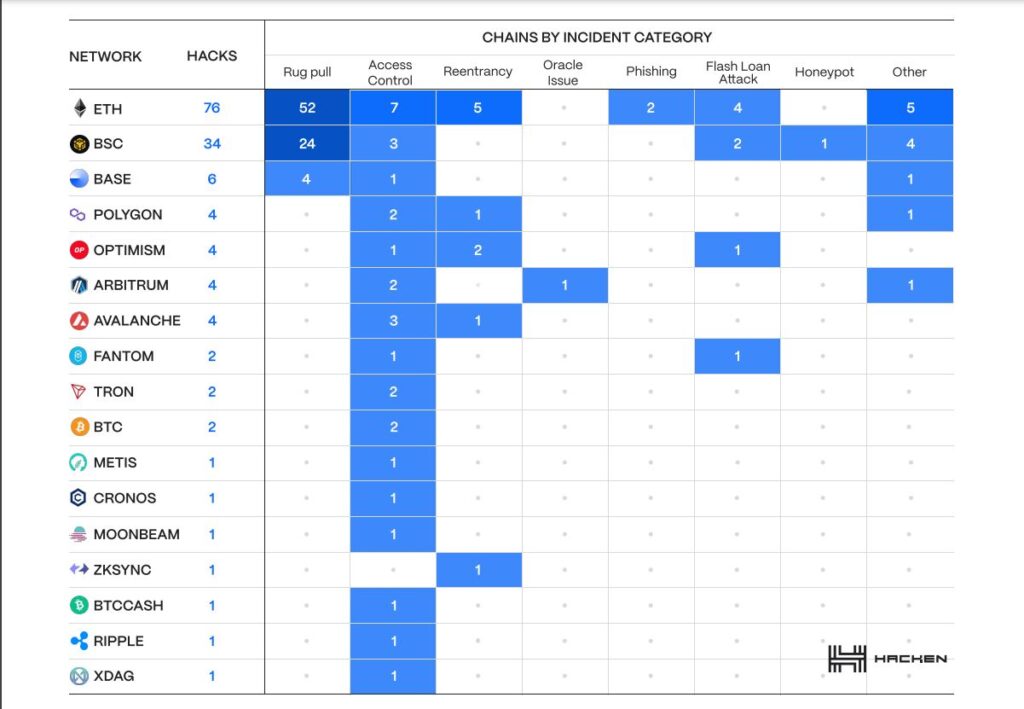
In a new report, Hacken, a leading Web3 security firm, has revealed that access control vulnerabilities were the most damaging type of exploit in Q3 2023, accounting for 65% of all financial losses. Rug pulls also remained prevalent, with 78 incidents reported.
The report, which was compiled using data from Hacken’s Trust Army, a community of researchers and security experts, provides a comprehensive overview of the most prevalent crypto hacks and scams during the quarter.
Access Control Vulnerabilities: The Most Damaging Type of Exploit
Access control vulnerabilities are flaws in the systems that govern who can access and modify digital assets. These vulnerabilities can be exploited by hackers to gain unauthorized access to private keys and seed phrases, which can then be used to steal assets from both smart contracts and externally owned addresses (EOAs).
The report highlights two notable examples of access control breaches in Q3 2023:
- Multichain: The Multichain bridge was exploited in September, resulting in the theft of $231 million in cryptocurrency. The exploit was made possible by a vulnerability in the bridge’s access control system, which allowed the attacker to gain unauthorized access to private keys.
- Mixin Network: Mixin Network, a crypto payment provider, lost approximately $200 million in a hack in September. The attack was also caused by a vulnerability in the company’s access control system, which allowed the attacker to gain unauthorized access to private keys.
Rug Pulls: A Simple Scam with a Big Impact
Rug pulls are a type of exit scam where developers abandon a project and steal investor funds. Rug pulls are often difficult to detect, as scammers may create fake websites and social media accounts to promote their projects.
The report found that rug pulls accounted for over 20% of all financial losses in Q3 2023. While the average loss per rug pull was relatively low ($638,594), the report notes that rug pulls are one of the simplest scams to prevent.
Stablecoin hacks
Stablecoins are cryptocurrencies that are pegged to a fiat currency, such as the US dollar. They are popular with investors because they are less volatile than other cryptocurrencies. However, stablecoins have also become a target for hackers in recent months. In Q3 2023, there were two major stablecoin hacks, resulting in the theft of over $200 million.
The report also highlights that no major platform or chain seems immune. While Ethereum was the top target, suffering over $313 million in losses, competitors like Binance Smart Chain, Polygon, Avalanche, and Fantom all endured millions in damages. Cross-chain bridges were also a hotbed for hacking.
Notable Hacks and Scams
In addition to the major trends discussed above, there were a number of other notable hacks and scams in Q3 2023. These included:
- The theft of $70 million from Curve Pools, Alchemix, and JPEG’d due to a bug in the Vyper compiler.
- A phishing scam that resulted in the theft of $24 million from crypto payment provider CoinsPaid.
- A liquidity drain attack on the Palm USD stablecoin, which resulted in the loss of $200,000.
Also read: Crypto Scams: A $3.3 Billion Threat to Investors in 2023 (So Far) – Learn How to Protect Yourself
Recommendations
The Hacken report provides a number of recommendations for crypto users and projects to help protect themselves from hacks and scams. These include:
- For users:
- Do your own research before investing in any project.
- Be wary of projects that promise unrealistic returns.
- Use strong passwords and two-factor authentication for all of your crypto accounts.
- Never share your private keys with anyone.
- For projects:
- Implement strong access control measures.
- Have your code audited by a qualified security firm.
- Be transparent with your community about any security incidents.
The Hacken report highlights the importance of security in the crypto space. Crypto users and projects should take all necessary precautions to protect themselves from hacks and scams.
By following the recommendations above, users and projects can help to reduce the risk of falling victim to these attacks.
I’m your translator between the financial Old World and the new frontier of crypto. After a career demystifying economics and markets, I enjoy elucidating crypto – from investment risks to earth-shaking potential. Let’s explore!


